0x00 前言
这道题貌似不止一种解法,挺有意思的一道题
0x01 程序分析
1 | mask@mask-virtual-machine:~/sangebaimao$ ./pwnme_k0 |
大致晓得了有啥功能,拉到IDA查看:
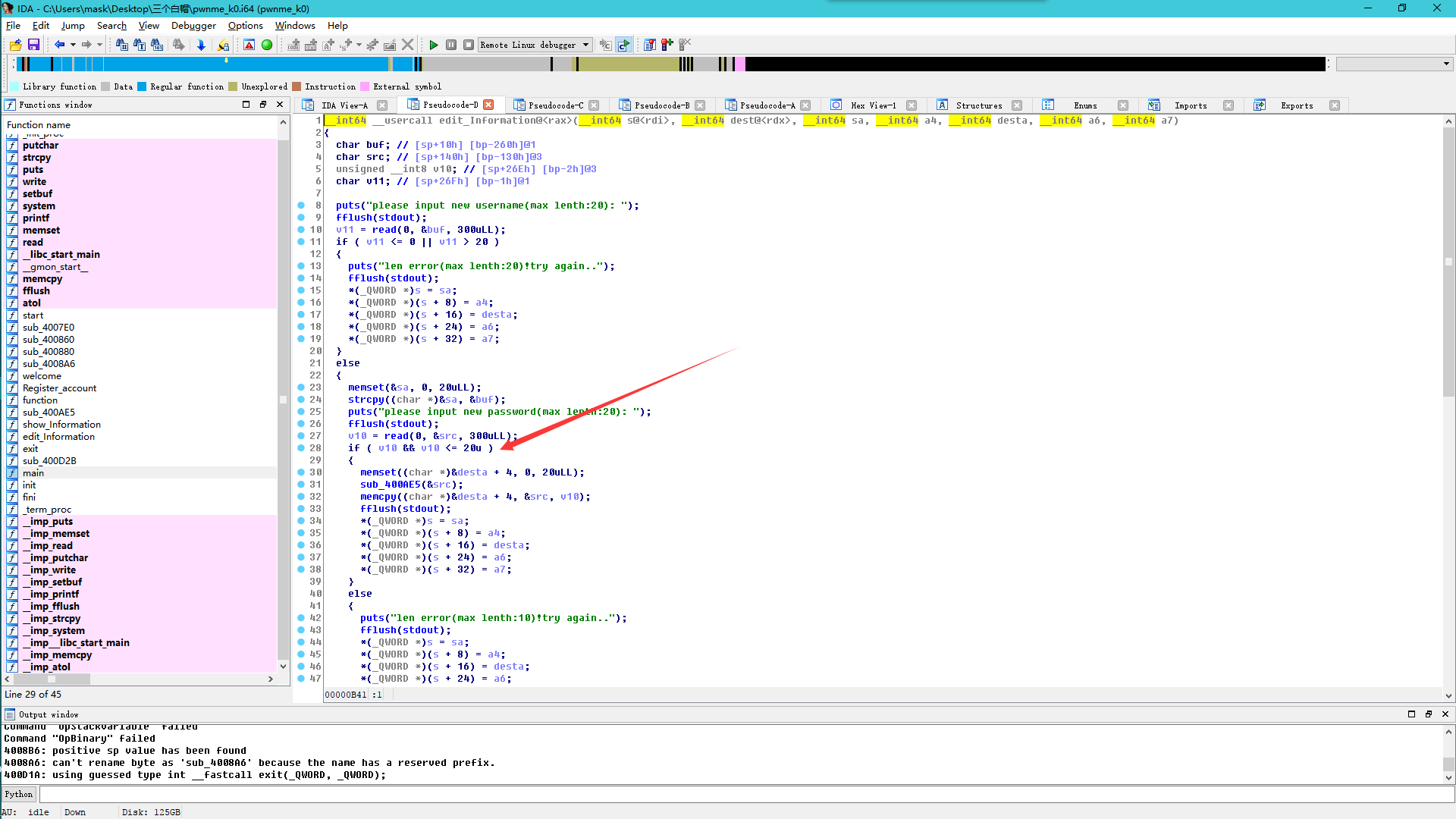
看到这,然后再切回反汇编窗口查看:
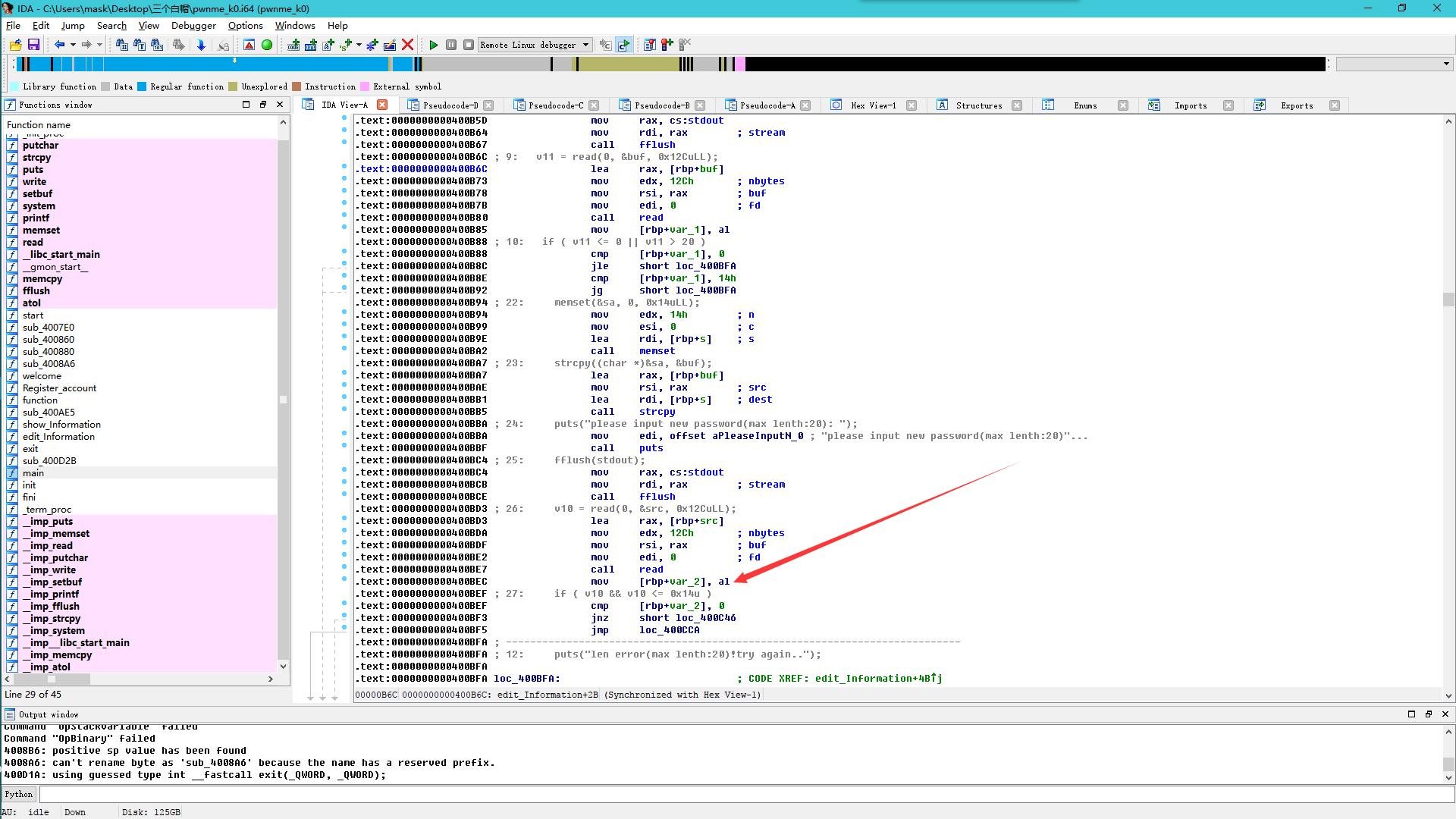
这里我之前也没有注意到,我当时想很像一个栈溢出漏洞,但是它这里检查了长度,我应该怎样去绕过,然后看了一下别人的wp,发现,靠,这里比较用的是前八个字节,那么就好办了,限制的长度为20个字节,也就是0x14,那么比如当我的长度为256时,也就是0x100,那么al存储的就是00,那么就绕过了长度检测
在看这,程序提供了一个可以利用的system("/bin/sh")调用,我们溢出后直接返回到这即可
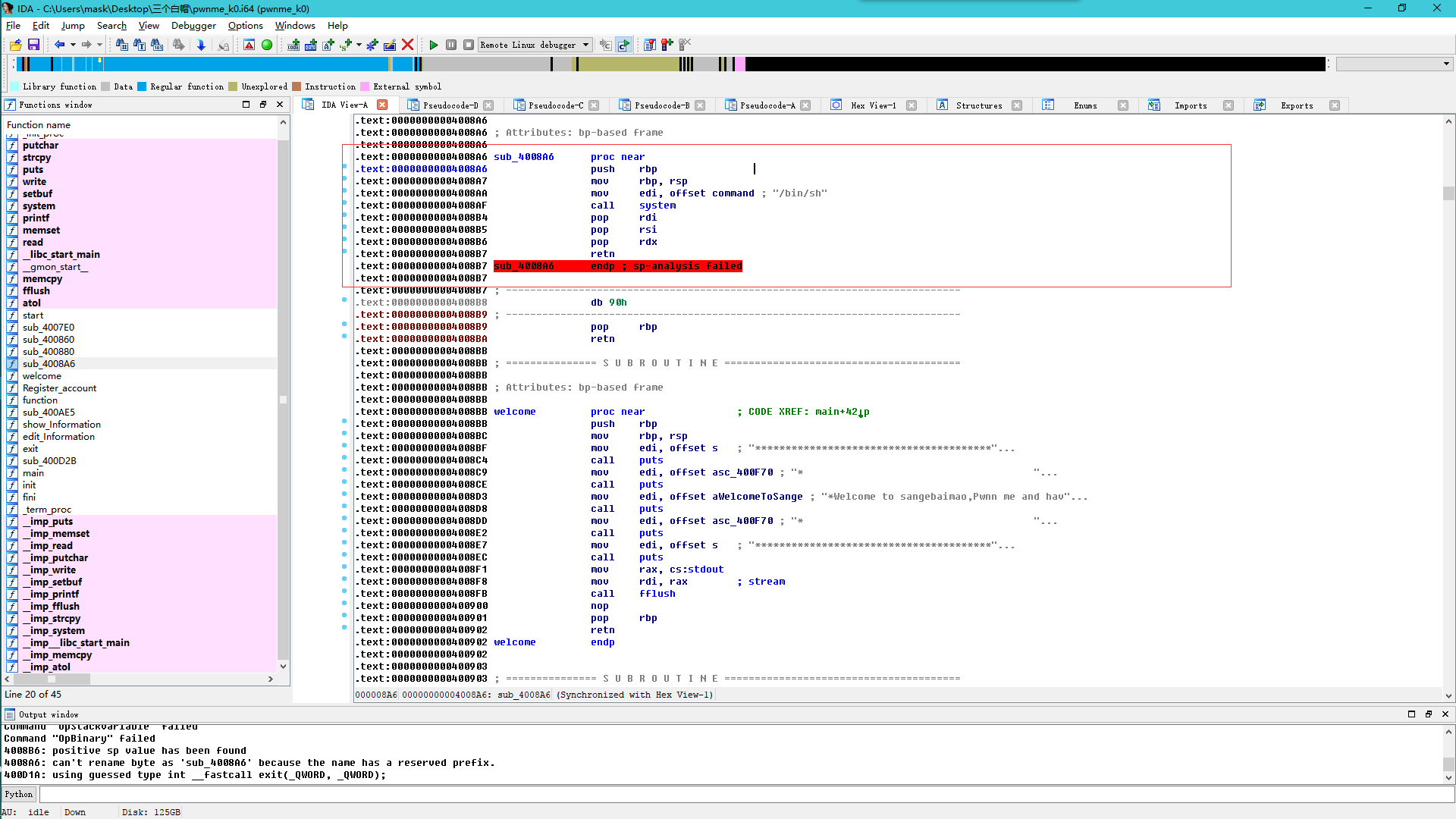
再来找找溢出的偏移:
1 | mask@mask-virtual-machine:~/sangebaimao$ gdb ./pwnme_k0 |
那么写一下exp:
1 | from pwn import * |
运行:
1 | mask@mask-virtual-machine:~/sangebaimao$ python exp.py |