Github:
https://github.com/scwuaptx/HITCON-Training
lab1
1 | #include <stdio.h> |
看题目提示是让我们熟悉工具的使用,那么这里直接修改逻辑就行
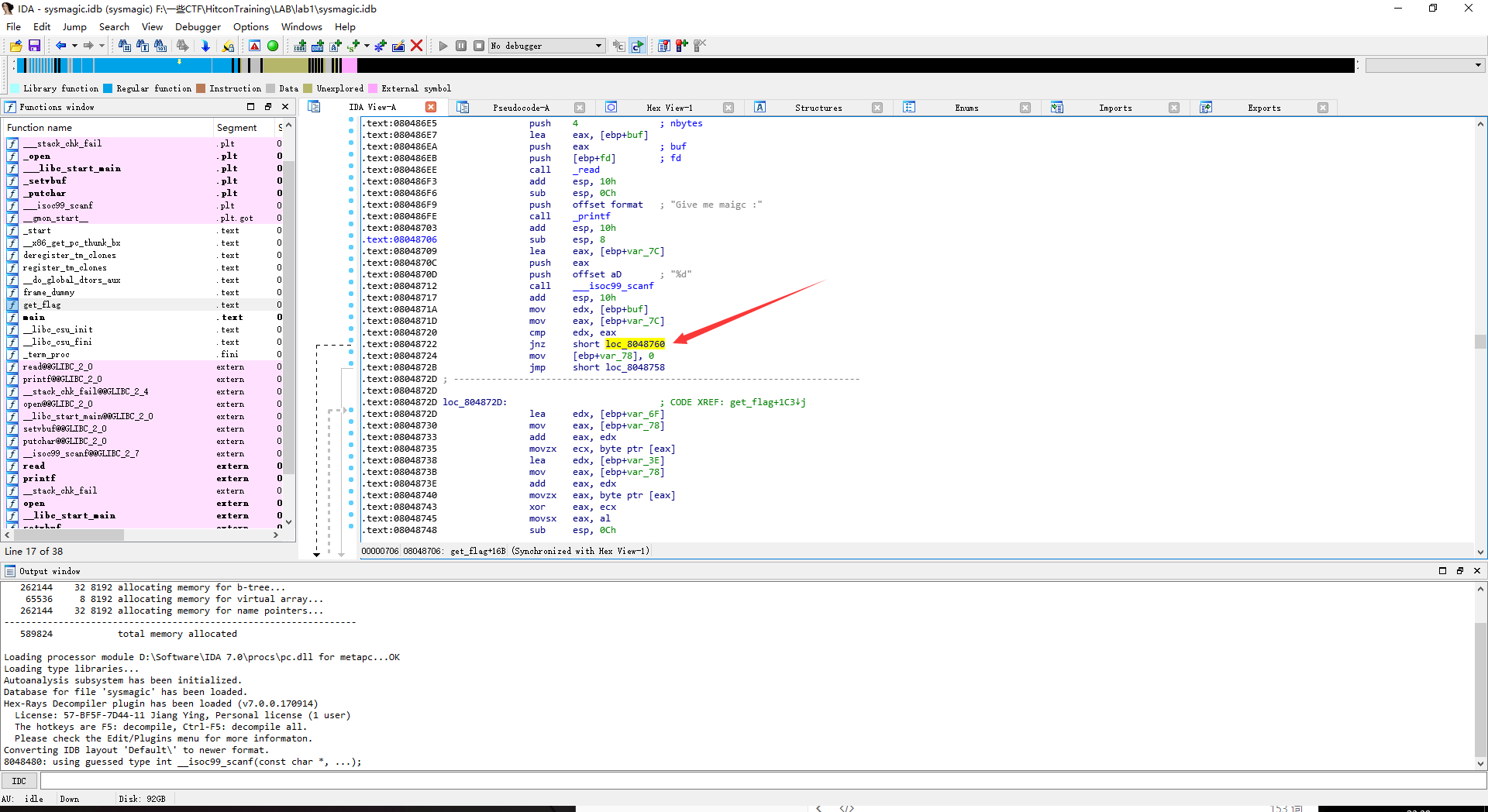
gdb下好断点
b *0x08048720
然后跑起来,修改eip的值为0x8048724
也就是让程序直接跳转到计算flag的流程中去
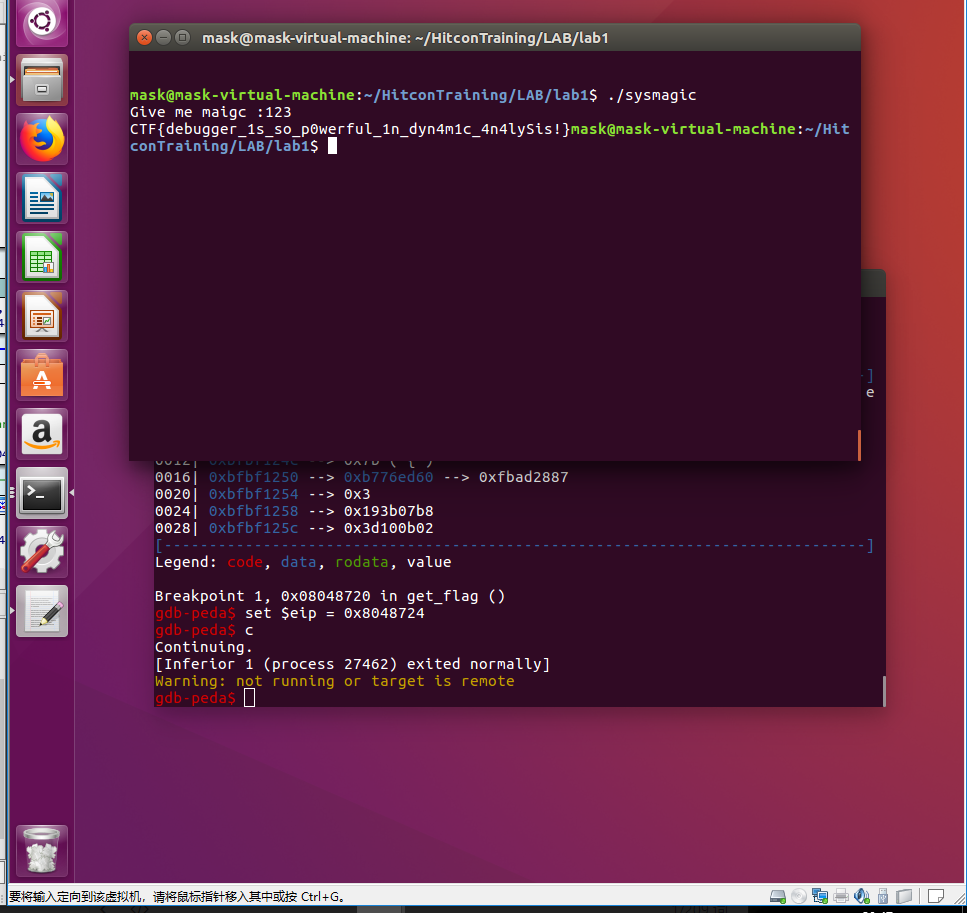
lab2
让我们输入shellcode然后执行
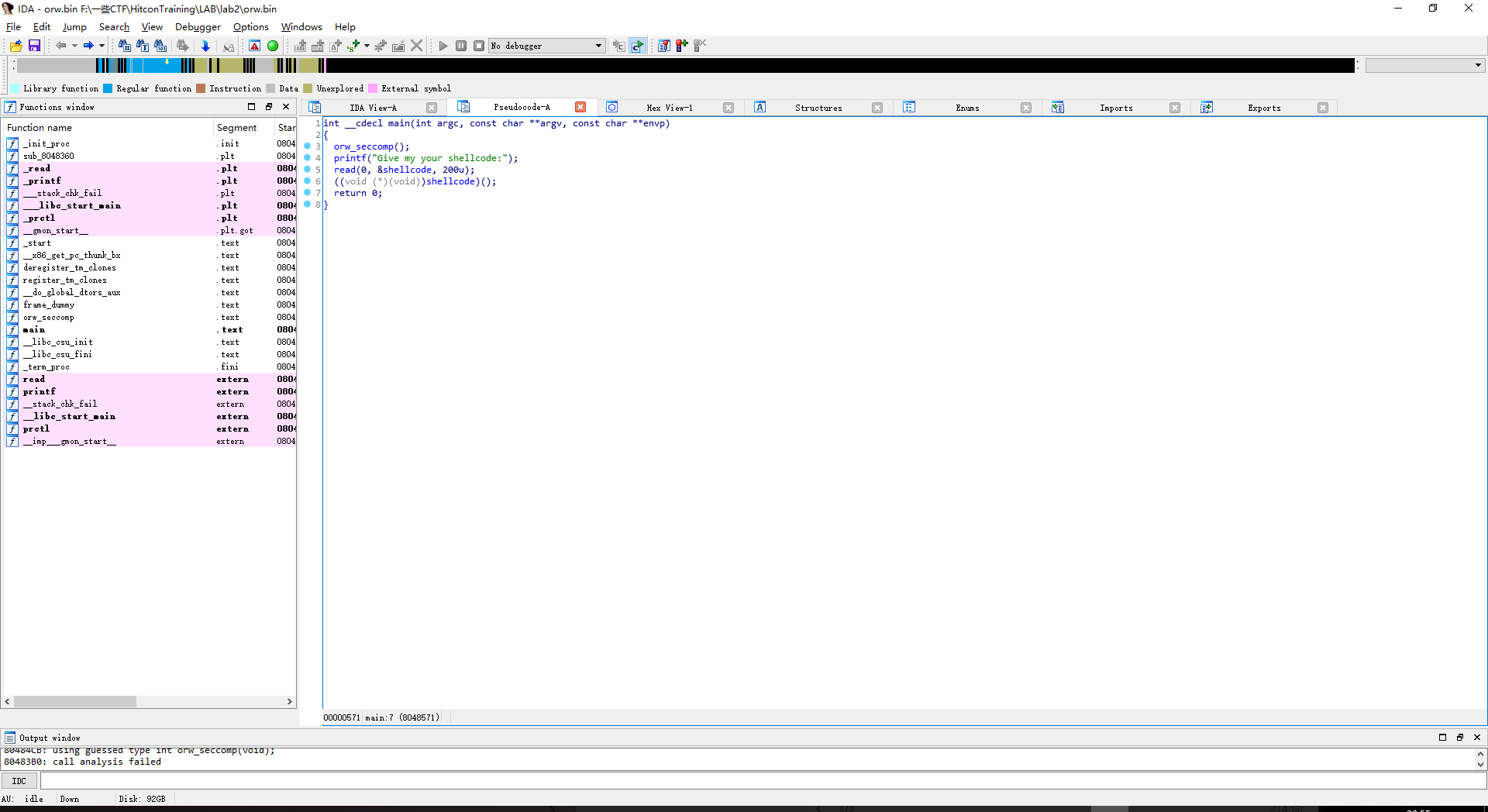
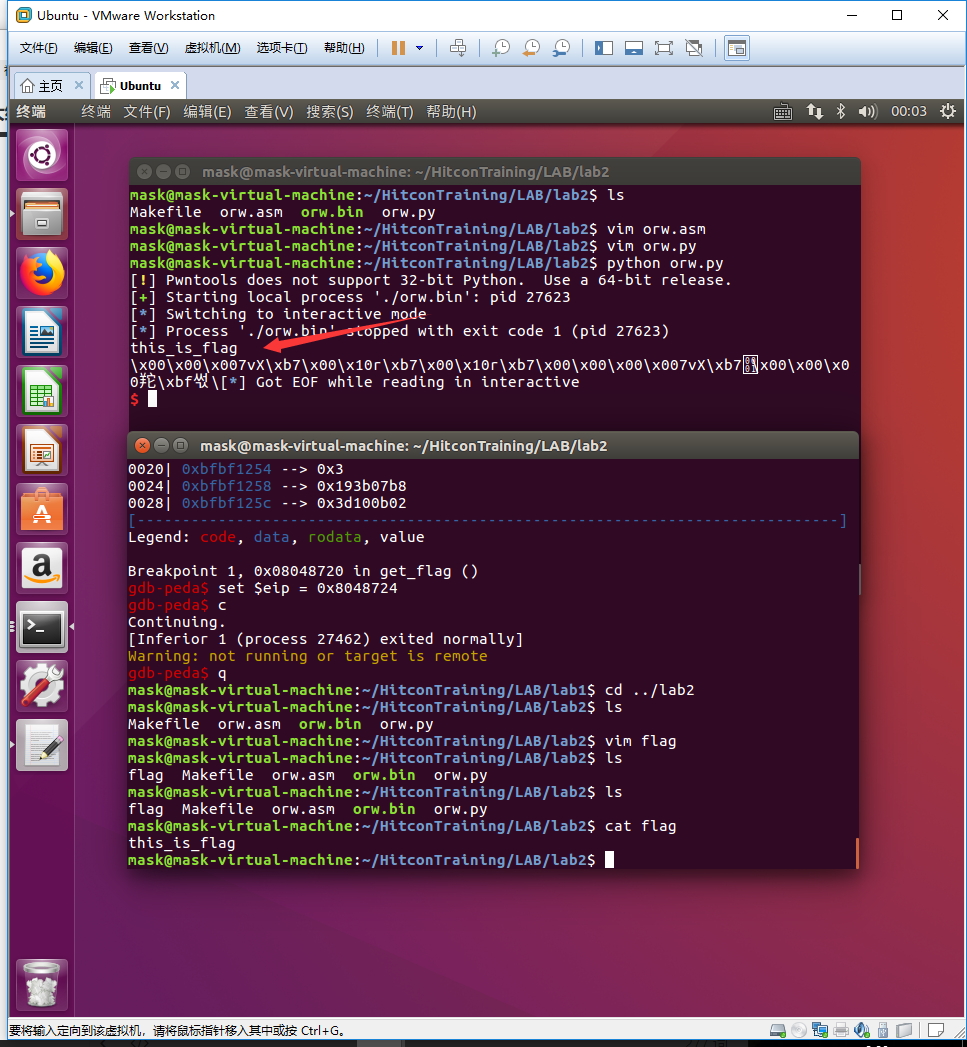
因为以前编写shellcode都是用生成的,所以就参考着给的答案自己再本地修改了下,新建了一个flag文件,然后运行修改后的shellcode
lab3
1 | #include <stdio.h> |
一个简单的栈溢出漏洞
1 | from pwn import * |